The NIS2 Directive, which updates and expands the EU’s Network and Information Systems Directive, places a strong emphasis on enhancing the security of network and information systems across various sectors. A key aspect of this directive is the implementation of robust access control measures.
Under the NIS2 Directive, there’s a focus on the need for security clearances as part of the access control requirements, especially for personnel who have access to critical network and information systems. This aspect is crucial for maintaining high-security standards and ensuring that sensitive information and critical infrastructure are protected.
In conclusion, within the NIS2 framework, the need for security clearances is a critical component of the access control strategy. It involves vetting and regularly reviewing the backgrounds of individuals who have access to critical systems, providing them with specialized training, and ensuring compliance with legal requirements. This approach enhances overall security by ensuring that only trusted and qualified individuals have access to sensitive information and critical infrastructure.
Introduction
Helisoft AB has developed a platform to handle security clearance and access control in line with NIS2 requirements, we call it Helios.
Helios can streamline and enhance the management of security clearances and access control in line with NIS2 requirements. Its capabilities in centralized management, automation, integration, */BAC, auditing, real-time monitoring, policy management, training, scalability, and data protection make it a valuable tool for organizations aiming to comply with the stringent access control standards set by the NIS2 Directive.
All capabilities provided by Helios are of course available any way your organization prefers to run these kinds of services, on-premise, at your cloud hyperscaler of choice or hybrid in any combination.
Continue reading for a detailed take on this challenge!
How security clearances fit into the NIS2’s access control framework?
The NIS2 Directive is very comprehensive so here’s a digest from the access control perspective, establishing a common ground of understanding going forward in this article.
- Security Clearances for Sensitive Roles: Personnel who are responsible for managing, operating, or accessing critical network and information systems may be required to undergo security clearances. This ensures that individuals with access to sensitive information or critical infrastructure have been thoroughly vetted.
- Background Checks: As part of the security clearance process, comprehensive background checks are conducted. These checks can include past employment verification, criminal record checks, and other relevant investigations to assess the trustworthiness and reliability of individuals.
- Regular Reviews: Security clearances are not a one-time procedure. Regular reviews and re-evaluations of personnel clearances are necessary to maintain security standards, especially when there are changes in job roles or security environments.
- Access Levels Based on Clearance: Access to certain information and systems can be restricted based on the level of security clearance an individual holds. This tiered access ensures that sensitive information and critical systems are only accessible to those who have been deemed trustworthy and have the requisite clearance level.
- Training on Handling Classified Information: Individuals with security clearances often receive specialized training on handling classified or sensitive information. This includes understanding the protocols for protecting such information and the consequences of security breaches.
- Compliance and Legal Obligations: Organizations must comply with legal and regulatory requirements regarding security clearances. This compliance is especially important in sectors where national security is a concern.
- Incident Reporting and Response: Part of the security clearance protocol involves training on incident reporting and response. Personnel with clearances are typically required to report any security incidents or vulnerabilities that they identify.
- Contractor and Third-Party Clearances: Security clearance requirements also extend to contractors and third-party service providers who access or manage critical systems or sensitive information.
How can Helios help with this?
Helios, as a platform designed for information governance, can significantly aid organizations in managing access control, particularly in the context of security clearances as required by the NIS2 Directive. Here’s how Helios can be beneficial:
- Centralized Management of Security Clearances: Helios can serve as a centralized repository for all security clearance records, making it easier for organizations to manage and track the clearance status of employees, contractors, and third-party vendors.
- Automated Clearance Verification: Helios automates the process of verifying security clearances, ensuring that individuals accessing sensitive information or systems have the necessary authorization. This automation reduces manual errors and streamlines the process.
- Integration with HR and Security Systems: Helios can integrate with HR systems to ensure that any changes in employment status, roles, or clearance levels are automatically reflected in access control permissions. Integration with security systems can also help in monitoring access and enforcing policies.
- Access Control (*/BAC) Enforcement: Helios can support */BAC by ensuring that access permissions align with an individual’s role and security clearance level. This ensures that employees can only access information and systems relevant to their role and clearance.
- Real-Time Alerts and Monitoring: Helios provides real-time alerts and monitoring for any unauthorized access attempts or deviations from established access control policies, enabling quick response to potential security incidents.
- Policy Management and Compliance Tracking: Organizations can use Helios to manage access control policies and track compliance with NIS2 requirements. The platform can be configured to ensure that policies are consistently applied across the organization.
- Data Protection and Privacy Compliance: Helios can help ensure that the handling of personal and sensitive information related to security clearances complies with data protection and privacy laws, which is a critical aspect of NIS2. This is especially important when using cloud services where Helios can safeguard data making sure that only the intended information is shared with the cloud service provider.
Practical real-world example!
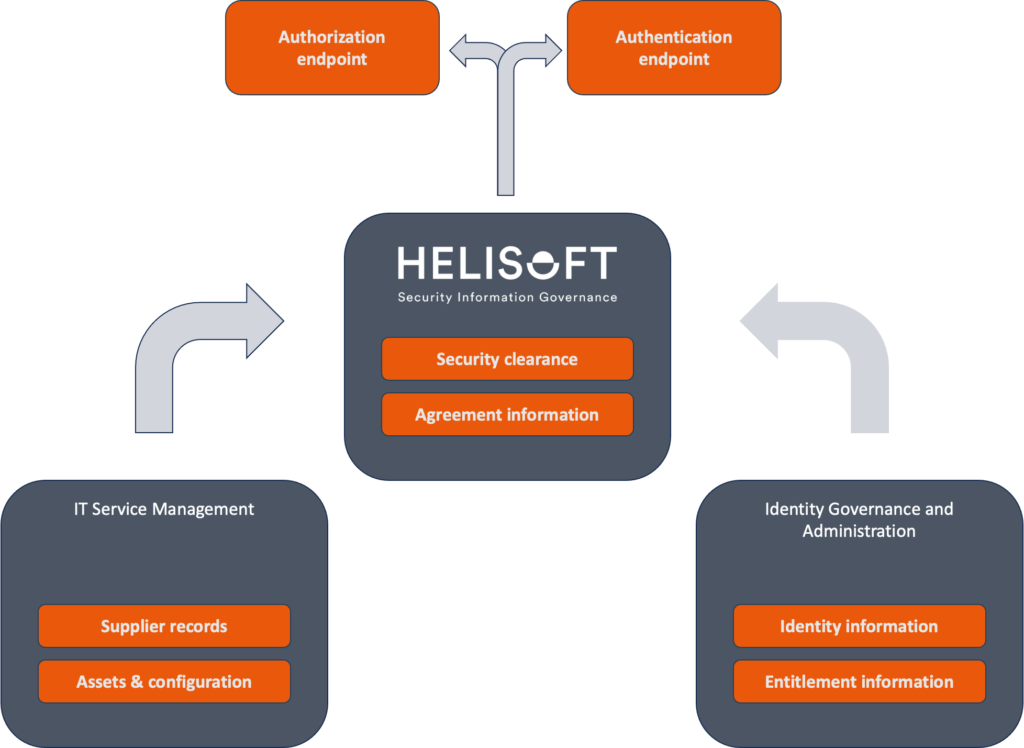
In this scenario, Helios, a ITSM tool of choice, and an IGA tool work together seamlessly to ensure comprehensive security and compliance management. Helios manages security clearances and agreements, ITSM tool handles supplier information and asset management, and the IGA tool takes care of identity and entitlements. This integration ensures that the organization can effectively manage access control, maintain compliance with the NIS2 Directive, and securely manage its extensive network of internal and external stakeholders.
Background: A large multinational corporation in the energy sector needs to ensure compliance with NIS2 Directive, manage its numerous suppliers, and securely handle its internal and external access control.
Role of Helios: Security Clearances and Agreement Information
- Security Clearance Management: Helios is used to manage security clearances for employees who access sensitive information. It stores clearance levels and agreement information securely.
- Vendor Agreement Compliance: Helios also keeps track of agreements with vendors, ensuring that they adhere to security requirements as outlined in these agreements.

Role of IGA: Identity and Entitlements Management
- Identity Management: The IGA tool is responsible for managing the identities of all employees, contractors, and third parties. It handles the creation, modification, and deletion of user accounts.
- Entitlements and Access Control: The IGA tool also manages user entitlements, ensuring that access rights are aligned with individual roles, responsibilities, and security clearances. It enforces least privilege access based on these roles.

Role of ITSM tool: Supplier Records and Asset Information
- Supplier Management: The ITSM tool is utilized to maintain detailed records of all suppliers. It includes information about contracts, service levels, and compliance with the organization’s security policies.
- Asset Management: The ITSM CMDB (Configuration Management Database) is used to keep an inventory of all IT assets. This includes servers, workstations, network devices, and the critical systems they support.

Integration and Workflow
- Onboarding a New Supplier:
- ITSM tool captures the new supplier’s information and contract details.
- Helios checks the supplier’s agreement for compliance with security standards.
- The IGA tool creates identities for supplier personnel who need access to the corporate network, assigning entitlements based on the minimum necessary access.
- Employee Security Clearance:
- An employee’s security clearance level is updated in Helios.
- The IGA tool receives this information and adjusts the employee’s access rights accordingly, granting or revoking access to certain assets tracked in ITSM tool.
- Auditing and Compliance:
- Helios generates reports on security clearance compliance and vendor agreement adherence.
- ITSM tool provides asset and supplier compliance reports.
- The IGA tool offers detailed logs of identity and access management, showing who had access to what, and when.
- Incident Response:
- If a security breach is detected, the IGA tool identifies the compromised identity.
- Helios verifies whether the breach involved someone with a specific clearance level or a vendor.
- ITSM tool aids in determining which assets were affected and initiates the incident response process.
So, bringing it all together, making use of the aggregated information thru Helios modern and secure API is an easy task. In addition to the authorization and authentication use-cases shown in the picture below, there could also be a good idea to integrate the IGA tool with the authorization endpoint so when users request entitlements that require an active security clearance, it will all hold together in a orderly manner.