Executive summary
In this document, we have explored the possibilities of combining Axiomatics attribute-based access control (ABAC) solution with Helios as a policy information point (PIP). ABAC allows organizations to meet a broad set of regulatory requirements by dynamically evaluating authorization information at runtime, providing fine-grained access control.
Helios offers a comprehensive platform for implementing a PIP, allowing organizations to create a super PIP with additional capabilities such as approval flows on attribute change, distributed cache, and dynamic APIs on every model created. With Helios, any organization can easily implement a policy information point, enabling them to control access to sensitive information effectively.
By combining Axiomatics’ ABAC with Helios’ PIP, organizations can achieve complete control over who can access sensitive information, and when. Helios’ virtual objects allow for information endpoints to be created specifically for each use case without the need to modify the underlying information model, providing a flexible and scalable solution for controlling access to sensitive data.
Overall, this integration provides organizations with a powerful tool for implementing a comprehensive access control solution, allowing them to meet regulatory requirements and protect sensitive information.
Scenario
In this scenario, not so theoretical as you might think, a customer has confidential data spread in several applications. According to internal guidelines regarding sensitive information, only authorized users should be able to consume confidential information which means that only employees working with the customer (by agreement) can access the information regarding that customer.
Furthermore, it should also be possible to specify which type of information the employee can access for each customer. We will use agreements to reflect which customer and which resource(s) an employee can work with per customer. In this scenario we will enable Axiomatics Decision Service (ADS) together with Helios to determine if an employee can access information for customers. Applications at our company will be able to send policy requests to ADS containing minimal information, such as Username, CustomerId and Resource type. ADS will use Policy Information Points to fill in the gaps of information. Helios DynamicAPI is a perfect match to be used as a PIP, and by utilizing virtual objects we can provide ADS with the information it needs at runtime without the need of changing the underlying information or model.
Implementation
Data model
The first step in implementing this scenario is to design a data model that includes all the necessary information for each customer and their respective resources. In this example, we will use Helios to create our data model. We start by defining objects with attributes and possible relationships.
One object that we need to define is the Identity object. This object will contain the following attributes:
- Display Name
- This attribute represents the name that will be displayed to other users when they view the identity. We automatically generate the display name by combining the First name and Last name attributes.
- Last name
- First name
- Username
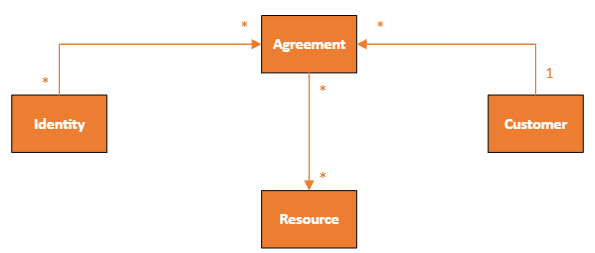
Virtual object
Helios automatically creates API endpoints based on our data model. This means that you can access data using HTTP requests without having to write any code. In this case, we also want an easy way for ADS to consume the combination of identity, agreement, customer, and resource. We can do that by configuring a Virtual object in Helios.
Virtual Objects provide a layer of abstraction on top of your data model, allowing you to combine data from multiple objects in your data model into a single, unified virtual object that can be queried like any other object. The virtual object is generated at runtime and is not stored in Helios.
In this scenario, we will create a virtual object that combines information from the Identity, Agreement, Customer, and Resource objects to provide a complete picture of who can access a particular resource.
By combining this information into a single virtual object, Helios not only simplifies the policy enforcement process but also streamlines the creation and management of policies themselves. This approach supports collaboration between business analysts and helps align business policies with technical implementations, improving the management of access to sensitive information while maintaining compliance with industry standards.
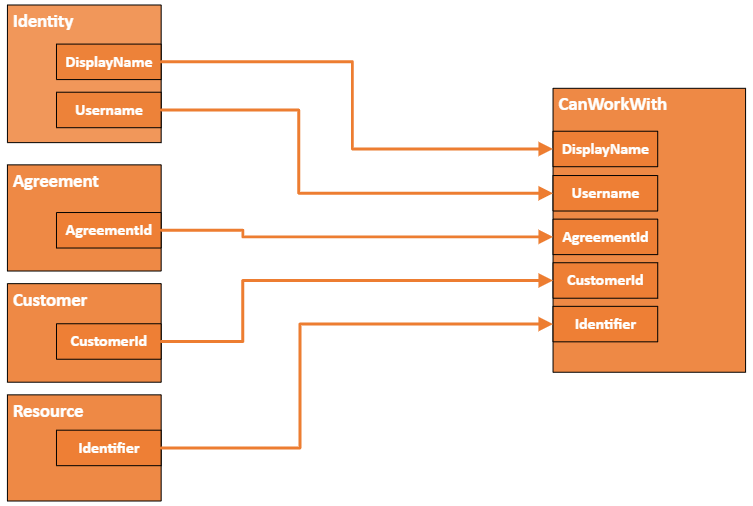
Policy
Once the data model and virtual objects are configured in Helios, the next step is to create policies that define the authorization logic. The policy needs to check whether the employee has the authorization to access the requested resource.
In this scenario, we create a policy that checks whether the employee has an agreement with the customer that allows access to the information type of the resource. The policy evaluates the attributes provided in the request, such as the user’s username and the resource’s customer ID and type.
If the application does not provide the attribute user.agreement.resourceType, ADS will use the username and resource customer ID to make a request to Helios DynamicAPI to retrieve a list of resource types that the identity is allowed to work with for that customer. This is done by adding a URL filter in the policy that asks Helios to give us a list of agreements assigned to the user and the customer.
Based on this information, the policy will either allow or deny the request for access to the resource. If the policy allows the request, the user will be able to access the confidential information for the specified customer and resource type. If the policy denies the request, the user will not have access to the information.
Alfa policy
namespace sensitiveCustomerInformation {
policy permitIfUserHasAgreement {
apply denyUnlessPermit
rule {
condition stringIsIn(stringOneAndOnly(resource.resourceType),user.agreement.resourceType)
permit
}
}
}
Helios PIP
One possible PIP that can be used with Axiomatics is Helios DynamicAPI. This powerful tool can provide ADS with the information it needs at runtime without the need for changing the underlying information or model. By leveraging Helios DynamicAPI, organizations can easily provide additional contextual information about users and resources that can be used to make better access control decisions.
We configured Helios DynamicAPI to expose a virtual object that contains attributes from: identity, agreement, customer and resource, the result should be provided “flattened”, so each combination of identity, agreement, customer and resource is returned, making it easy to be used in our Alfa policy.
We can now use the Virtual Object endpoint CanWorkWith to fetch each combination of identity, customer, resource and agreement together with a http filter to get what type of information Bryson Thompson can work with for the customer UpData.
GET Request:
http://localhost:44356/json/CanWorkWith?filter=Username eq “rja110” and CustomerId eq “UpData”
Response:
[
{
"Identifier": "QuarterlyReport",
"CustomerId": "UpData",
"AgreementId": "UpDataFinacialReporting#1",
"Username": "rja110",
"DisplayName": "Bryson Thompson"
},
{
"Identifier": "Invoice",
"CustomerId": "UpData",
"AgreementId": "UpDataFinacialReporting#1",
"Username": "rja110",
"DisplayName": "Bryson Thompson"
}
]
Conclusion
Combining Axiomatics externalized fine-grained authorization with Helios DynamicAPI enables organizations to achieve complete control over who can access confidential information. The use of virtual objects allows information endpoints to be tailored to specific use cases without altering the underlying information model. By using Helios satellites to fetch identity information from HR systems, another layer of security can be added to the authorization process. This ensures that only current employees with proper access are able to view the confidential information.
Moreover, by applying holistic governance to security-related ABAC components, organizations can embrace a paradigm shift in access control. By using a holistic approach to access control, organizations can establish a unified policy framework that spans across multiple applications, departments, and systems. This allows businesses to ensure that all sensitive information is protected and accessed only by those with the proper permissions.
In today’s world, where data breaches and cyber-attacks are a constant threat, it is more important than ever for businesses to protect their sensitive information. By leveraging the powerful tools provided by Axiomatics and Helios, organizations can ensure that confidential information is only accessed by authorized employees while still being easily accessible to those who need it. This results in a secure and efficient system that benefits both the organization and its workforce.
To sum up, leveraging Axiomatics and Helios tools for access control and policy enforcement offers a formidable solution for organizations striving to protect their confidential data. By embracing a holistic approach to access control, businesses can create a unified policy framework spanning across various applications, departments, and systems. Armed with these powerful tools, organizations can confidently protect their data and ensure compliance with internal and external guidelines for handling sensitive information.


