I’ve always appreciated the architectural models, governance guidelines, and best practices developed by U.S. agencies like NIST and CISA. These frameworks play a critical role in shaping an organization’s cybersecurity posture and reducing exposure to threats.
One concept gaining momentum is Zero Trust Architecture (ZTA), as defined by NIST. It serves as a strategic lens for connecting cyber threats, security initiatives, and risk management. Supporting this are the NIST Cybersecurity Framework (CSF) and CISA’s Zero Trust Maturity Model (ZTMM), which add structure and actionable guidance for implementation. You’ll find a summary and reference links at the end of this post.
These frameworks are especially valuable for organizations aiming to proactively enhance their security maturity. They complement regulatory efforts from the EU—such as GDPR, DORA, NIS2, and the AI Act—which provide critical compliance structures but are often more reactive.
CISA captures the essence of Zero Trust well:
“Zero trust presents a shift from a location-centric model to an identity, context, and data-centric approach… fundamentally, it may require a change in an organization’s cybersecurity philosophy and culture.”
Adopting a Zero Trust approach can feel daunting. Identifying where to start, prioritizing efforts, and building internal alignment are common challenges. Technology alone is not the answer – organizational alignment and cultural change are far more critical and complex.
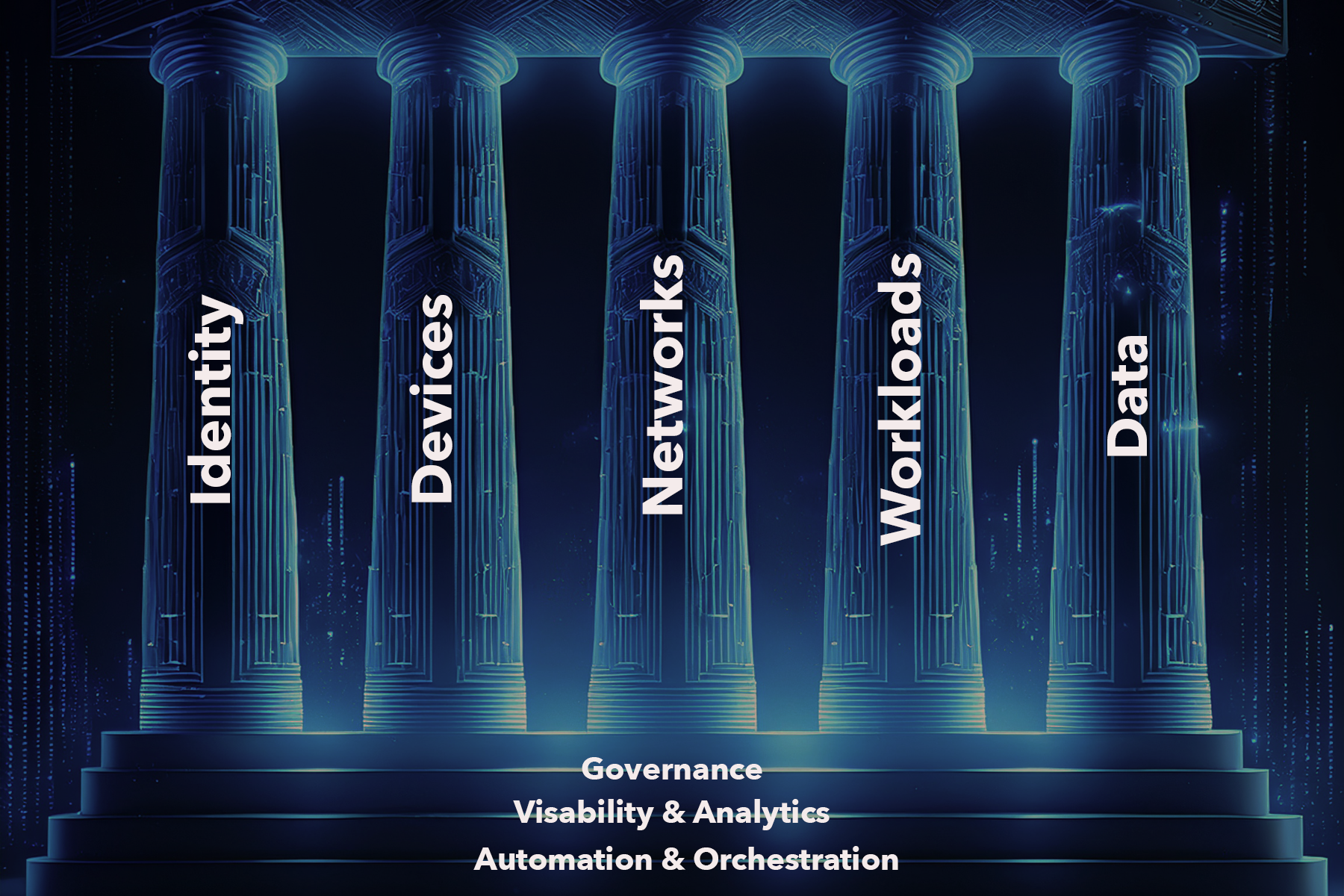
That’s where CISA’s ZTMM becomes essential. It offers a framework for setting goals and charting a path forward. ZTMM is built on five pillars:
- Identity
- Devices
- Networks/Environment
- Applications/Workloads
- Data
… and supported by three cross-cutting capabilities:
- Visibility & Analytics
- Automation & Orchestration
- Governance
These cross-cutting elements are the glue that integrates the pillars into a cohesive, ecosystem.
At Helisoft, we support organizations with complex information security needs. Our platform, Helios, is a robust, data-centric security and governance tool. It enables orchestration, workflow automation, and governance oversight – ideally suited to bridging ZTMM pillars.
Helios integrates cross-domain data and provides a contextual data layer that flexibly models your enterprise’s cybersecurity ecosystem, encompassing users, devices, networks, applications, and data. This “identity fabric” can be used for both operational use and makes governance transparent to auditors and business stakeholders alike.
Our approach enables organizations to focus on the use cases that need immediate attention. But the model can easily grow to support wider organizational challenges and facilitate the transformation towards a desired modern security posture.
Examples
Achieving the full benefits of an identity fabric requires a data-centric approach—one that relies on a common information model spanning all key pillars. Once the data is normalized, qualified, and readily available, it can be leveraged to drive a wide range of initiatives. A few examples are outlined below.
Identity – Identity data is often fragmented, residing in silos such as LDAP directories, IGA repositories, and HR databases, each serving specific purposes. Typically, this data is not centrally accessible and lacks standardized API interfaces for integration with other systems and processes.
The Helios information model goes beyond traditional identity data by capturing the full ecosystem, including relationships to both digital resources and physical assets. This encompasses organizational entities, compliance control points, documents, encryption keys, cabinets, buildings, and more.
By enabling secure access to this distributed identity data, we can begin to feed qualified, contextual information into systems that rely on it. These may include core IAM services as well as adjacent systems that benefit from a broader, contextual identity perspective.
With this comprehensive data model in place, we can enable and automate new types of identity-driven workflows – such as security clearance processes for external subcontractors or scenarios involving physical access management.
Devices – Device management solutions hold valuable data on device health and compliance. But devices often remain disconnected from identity systems and access policies. By integrating with Helios, contextual device attributes can be linked to user identities, creating a unified view for policy decisions. Helios can also expose device risk information to other systems, enabling ABAC and PBAC solutions to factor in real-time device compliance and risk status, ensuring that access decisions reflect both the user’s identity and the security status of their device at the time of access.
Networks – VPN services traditionally authenticate users based on credentials alone, lacking deeper contextual awareness of user status or organizational relationships. By integrating with Helios, a VPN service can dynamically query security clearance levels and subcontractor affiliations before granting network access.
For example, access to Red, Orange, or Green network segments can be enforced based on attributes retrieved from Helios. Users with high security clearance may access Red segments, while subcontractors with limited trust are confined to Green or Orange zones. This enables dynamic, attribute-driven network segmentation, ensuring that connections are granted only when identity, role, and organizational context align with the security requirements of each segment.
Applications and Workloads – Ensuring continuous compliance across an application’s lifecycle is often challenging, with control requirements scattered across frameworks and lacking integration into operational processes. Helios addresses this by ingesting various compliance frameworks and linking different control points directly to information objects, which are in turn connected to applications and workloads.
This allows application owners to perform targeted reviews, responding to applicable control points for their specific applications. By embedding these compliance checkpoints into the application lifecycle, organizations gain real-time assurance that security and regulatory requirements are continuously met. This enhances Zero Trust by ensuring that not only identities and devices are verified, but that applications themselves are continuously assessed and governed before being trusted within the environment.
Data – By leveraging the platform’s connector service to ingest and normalize data, we can build a data fabric that enables comprehensive visualization of the ZTA data ecosystem. This visualization layer transforms raw data into actionable insights, supporting operational efficiency and policy-driven data governance. It forms the foundation for secure data consumption aligned with governance requirements.
The identity fabric functions as a data catalog, maintaining an inventory of available data. As outlined above, this data can be utilized for a variety of use cases, including dynamic access control and physical access. Additionally, data orchestration is possible through event-based signals. The Helios platform can operate as both a producer and subscriber of these signals, facilitating communication across siloed systems. This capability supports the implementation of a loosely-coupled architecture – an essential characteristic of a modern Zero Trust Architecture (ZTA) model.
You will find summaries and links to the NIST and CISA publications below.
Zero Trust Architecture (ZTA), as defined by NIST, is a cybersecurity framework that assumes no implicit trust for any user, device, or system, whether inside or outside the network perimeter. Access to resources is granted based on continuous verification of identity, device posture, and contextual factors such as location and behavior. The architecture emphasizes least privilege access, strict authentication, and dynamic policy enforcement to reduce the attack surface and limit potential breaches.
https://nvlpubs.nist.gov/nistpubs/specialpublications/NIST.SP.800-207.pdf
The NIST Cybersecurity Framework (CSF) 2.0 provides a comprehensive, flexible approach to managing cybersecurity risk across sectors and organization sizes. It is organized around six core functions—Govern, Identify, Protect, Detect, Respond, and Recover—which together help organizations understand, manage, and reduce cyber risk. CSF 2.0 emphasizes governance, supply chain risk, and outcome-based security, serving as a strategic guide for building and maintaining a robust cybersecurity posture.
https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf
The CISA Zero Trust Maturity Model (ZZMM) provides a framework for organizations to assess their progress in implementing a Zero Trust Architecture (ZTA). It defines five maturity levels that help organizations progressively adopt and refine Zero Trust principles, such as continuous verification and least-privilege access. The model is structured around five key pillars: Identity, Devices, Networks/Environment, Applications/Workloads, and Data, guiding organizations to assess their current state, set improvement goals, and build a more secure, resilient infrastructure.
https://www.cisa.gov/sites/default/files/2023-04/CISA_Zero_Trust_Maturity_Model_Version_2_508c.pdf


